Budget Sharing: Relay is Up!
I’m very excited to announce the release of the Bucket Relay! It’s now much easier to share your budget between devices. Let me take you on a tour of how it works and how it keeps your data secure as it travels across the Internet.

Alice and Bob¶
To explain how this system works, let’s walk through connecting two devices: a phone and a laptop. In describing cryptographic communication systems, it’s common to use the fictional characters Alice and Bob, two people who want to talk securely.
In fact, most of the code tests for using the Buckets Relay feature Alice and Bob:
Let’s follow that convention: Alice has a laptop and Bob has a mobile phone. They just got married 🎉 and Alice wants to share the budget with Bob.

This might get long and technical, so if you don’t want to read it all, the gist is:
- Download the newest Beta version of Buckets to get access to the relay
- Sign up for an account on the relay, or use your Buckets license
- Read the instructions and get your budget on all your devices!
Buckets is Old School¶
If Buckets were a web app, Alice and Bob would just sign in to the website and we’d send their budget from our servers to their devices.
But Buckets isn’t a web app—it’s an old-school, downloaded, install-on-your-computer, no-subscription, completely private app. We don’t have Alice’s budget. Or your budget. (And, no offense, we don’t even want your budget. You can keep it 😁)
Instead, Bob’s phone needs to get the budget directly from Alice’s laptop. But how?
Where are you?¶
In the current version of Buckets, Alice can share the budget with Bob on their local home network. But it sometimes doesn’t work very well because of firewall and network configurations that prevent Alice’s laptop from seeing Bob’s phone. Both devices might never connect, wondering where the other is.
This is where the Buckets Relay comes in. It’s a central server that Alice and Bob can connect to so their laptop and phone can find each other.
How can a shared server be secure?¶
“Wait a second,” Alice says, “how can that be secure? I thought Buckets didn’t store our budget.”
“Alice,” I reply, “I didn’t know you had a speaking part in this article!”
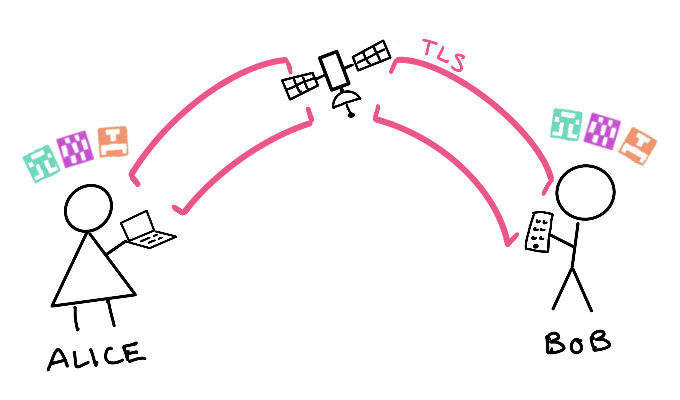
The relay doesn’t store your budget. In fact, as I’ll show you below, the relay can’t see your budget even as it passes it along. Think of the relay like a satellite orbiting the earth. Alice can bounce her budget off of the relay onto Bob’s phone.
Here’s how it works:
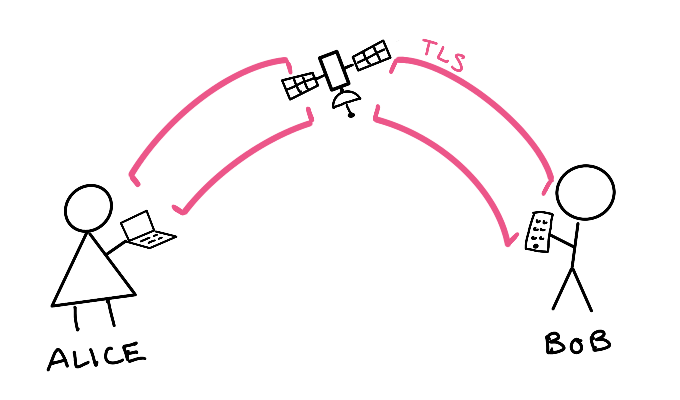
Step 1: Connect with TLS¶
Alice and Bob each connect to the relay with Transport Layer Security (TLS) on port 443, the standard HTTPS port. TLS is what your bank and every other website uses to encrypt communication between you and them. TLS provides an encrypted shield that prevents anyone on the Internet from snooping on or changing the information you send.
Step 2: Tell the relay who you are¶
The relay needs to know who its users are, to prevent people from using it for things unrelated to Buckets and to make it easy for you to connect your devices. So, the relay will know your email address.
Alice purchased a Buckets license years ago, so she and Bob decide to use her license to authenticate with the relay. If they were still using the trial version of Buckets, they could sign up for an account on the relay.
Step 3: Tell the relay who you are, again¶
Since Alice and Bob are sharing their license (which is totally fine, since they are members of the same immediate family living in the same house), the relay needs a way to distinguish which device it’s talking to.
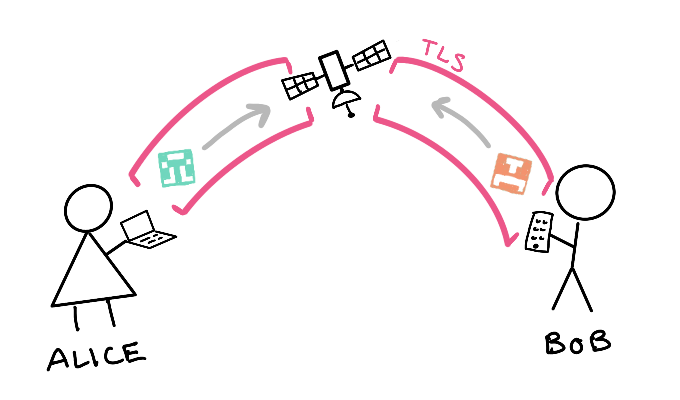
Alice’s laptop then generates a public and secret key pair. Public and secret keys can do two important things:
- If you have someone’s public key, you can use it to encrypt a message that can only be decrypted with the matching secret key.
- You can use your secret key to sign a message. Anyone who has your public key can verify that the message was signed with the secret key (even though they don’t have the secret key). This proves that the message was signed by you.
So Alice sends her public key to the relay as a kind of mailing address, essentially saying, “if anyone on the relay wants to talk to me, this public key is how to address me.”
Bob does the same.
Step 4: Connect the pair¶
Since Alice and Bob used the same license to sign in to the relay, the relay notifies Alice that Bob’s public key connected and notifies Bob that Alice’s public key connected. Alice and Bob see each other’s public keys in Buckets and decide to connect.
Each will then be shown some pairing images and codes that represent their public key, the other device’s public key, and a checksum. If the images and codes match, it means that future communication is guaranteed to only go to the people that possess the secret keys.
Alice now trusts Bob, Bob trusts Alice, and the relay is happy to pass data between the two.
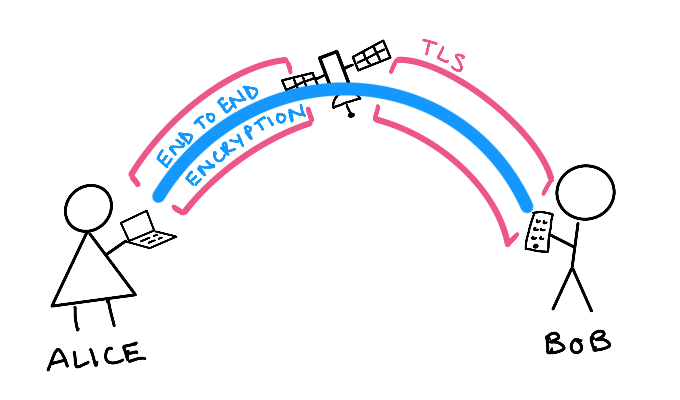
Step 5: More encryption, please!¶
But Alice and Bob don’t trust the relay. Rightly wary of some Internet Stranger hosting some server, they start yet another layer of encryption between themselves. This is achieved with a libsodium key exchange which allows Alice to encrypt messages that only Bob can decrypt, and vice versa.
With this encryption in place, the relay can no longer read anything they send to each other. Alice and Bob can communicate from one end to the other with complete privacy.
Step 6: Doubt¶
“Now, hold on,” Alice demands, arms folded and eyes narrowed. “I don’t believe you! I think your relay server actually saves our budget and sells the information! Probably to advertisers! They’re going to see all the money in our doughnut bucket and spam us with gooey, glazed specials and apple fritter ads!”
“Woah, Alice,” I respond. “I completely understand. But you don’t have to trust me. You can run a relay server yourself if you want. All the relay code is open source. Your doughnut bucket is safe.”

Other interesting stuff¶
One thing I’m quite happy about is the efficient way that Buckets sends budget files between devices. Budget files are normal SQLite files, and as such they are divided evenly into blocks, called pages. When Bob first requests the budget from Alice, the whole thing will be sent. But afterward, only the changed pages are sent. This is achieved by Bob sending Alice a short summary of the pages he has, and Alice responding with only what he’s missing. Since budgets tend to have new stuff added to the end more often than stuff changed in the middle, this should make syncing very fast.
Next steps¶
As mentioned previously, now that it’s easy for devices to share among themselves, the next step is to make it possible to alter the budget on multiple devices at the same time. After some bug fixes and possibly some other features, look for budget merging as the next major feature.
Happy Budgeting!
— Matt
I’m going to go get a doughnut.
Comments
